
HackBar Chrome 插件, crx 扩展下载

A browser extension for Penetration Testing
## Contributor
- 0140454
- GitHub: https://github.com/0140454
- lebr0nli
- GitHub: https://github.com/lebr0nli
- boylin0
- GitHub: https://github.com/boylin0
- HSwift
- GitHub: https://github.com/HSwift
## How to open it?
1. Open "Developer tools" (Press F12 or Ctrl+Shift+I)
2. Switch to "HackBar" tab
3. Enjoy it
## Features
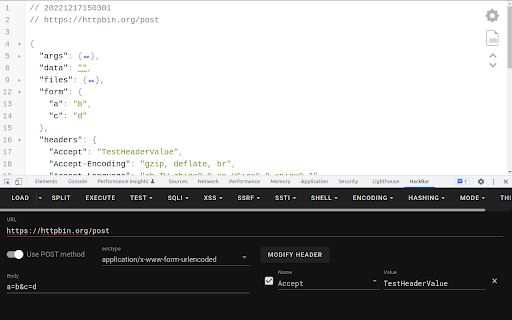
* Load
* From tab (default)
* From cURL command
* Supported
* HTTP methods
* GET
* POST
* application/x-www-form-urlencoded
* multipart/form-data
* application/json
* Request editing mode
* Basic
* Raw
* Custom payload
* For more information, please visit https://github.com/0140454/hackbar/blob/master/README.md
* Auto Test
* Common paths (Wordlist from dirsearch included)
* SQLi
* Dump all database names (MySQL, PostgreSQL, MSSQL)
* Dump tables from database (MySQL, PostgreSQL, MSSQL)
* Dump columns from database (MySQL, PostgreSQL, MSSQL)
* Union select statement (MySQL, PostgreSQL, MSSQL)
* Error-based injection statement (MySQL, PostgreSQL, MSSQL)
* Dump in one shot payload (MySQL)
* Reference: https://github.com/swisskyrepo/PayloadsAllTheThings
* Dump current query payload (MySQL)
* Reference: https://github.com/swisskyrepo/PayloadsAllTheThings
* Space to Inline comment
* XSS
* Vue.js XSS payloads
* Angular.js XSS payloads for strict CSP
* Some snippets for CTF
* Html encode/decode with hex/dec/entity name
* String.fromCharCode encode/decode
* Helper function for converting payload with `atob`
* LFI
* PHP wrapper - Base64
* SSRF
* AWS - IAM role name
* SSTI
* Jinja2 SSTI
* Flask RCE Reference: https://twitter.com/realgam3/status/1184747565415358469
* Java SSTI
* Shell
* Python reverse shell cheatsheet
* bash reverse shell cheatsheet
* nc reverse shell cheatsheet
* php reverse shell/web shell cheatsheet
* Encoding
* URL encode/decode
* Base64 encode/decode
* Hexadecimal encode/decode
* Unicode encode/decode
* Escape ASCII to hex/oct format
* Hashing
* MD5
* SHA1
* SHA256
* SHA384
* SHA512
## Shortcuts
* Load
* Default: Alt + A
* Split
* Default: Alt + S
* Execute
* Default: Alt + X
* Switch request editing mode
* Default: Alt + M
## Third-party Libraries
For more information, please visit https://github.com/0140454/hackbar#third-party-libraries
| 分类 | 💻开发者工具 |
| 插件标识 | ginpbkfigcoaokgflihfhhmglmbchinc |
| 平台 | Chrome |
| 评分 |
★★★★★
5
|
| 评分人数 | 3 |
| 插件主页 | https://chromewebstore.google.com/detail/hackbar/ginpbkfigcoaokgflihfhhmglmbchinc |
| 版本号 | 1.2.8 |
| 大小 | 1.72MiB |
| 官网下载次数 | 80000 |
| 下载地址 | |
| 更新时间 | 2024-12-30 00:00:00 |
CRX扩展文件安装方法
第1步: 打开Chrome浏览器的扩展程序
第2步:
在地址栏输入: chrome://extensions/
第3步: 开启右上角的【开发者模式】
第4步: 重启Chrome浏览器 (重要操作)
第5步: 重新打开扩展程序管理界面
第6步: 将下载的crx文件直接拖入页面完成安装
注意:请确保使用最新版本的Chrome浏览器
同类插件推荐

X情报查询助手
鼠标上的情报专家。简化查询流程,提升分析效率。步刻科技有限公司出品鼠标上的情报专家。简化查询流程,提

FindSomething
在网页的源代码或js中找到一些有趣的东西该工具用于快速在网页的html源码或js代码中提取一些有趣的

XSS辅助工具
XSS辅助工具wooyun原地址:http://zone.wooyun.org/content/76

Port Checker Tool
Is a free online tool to find open ports in your s

FOFA Pro View
FOFA Pro viewThe Fofa Pro View plugin tells you wh

hackbar
A browser extension for using kbar in HackMDHackba

XSS
Web Development toolA chrome extension tool that c

Admin tools
Whois, Port checker, Reverse IPIP Info, Domain Who

YesWeHack VDP Finder
This extension tells if visited sites have vulnera

CounterXSS
An Extension to counter XSS attack!A browser exten

HackBar
A browser extension for Penetration Testing## Cont

Hack-Tools
The all in one Red team extension for web penteste

OWASP Penetration Testing Kit
OWASP Penetration Testing KitThe Penetration Testi